What is Revenge Pornography?

As cited in the illustrious Cambridge Dictionary[1]. Revenge porn is private sexual photographs or filmography, in which are put onto the online environment by a former partner which depicts the sender of the images/films, with intent to punish or harm them.
For example, if an ex-boyfriend who had experienced a bad break-up uploads images of their former sexual partner, to a porn website or even social media and this has an extremely detrimental effect on that women.
Introduction
Revenge pornography is a fairly new but, rapidly expanding area of law in relation to the online environment. The reason for this is, growth of technology with several applications available on people-in particular teenager’s phones. These include; Snapchat, Instagram, Facebook and many more. This means it is very accessible for young people to interact and pass sexual images or videos to other young people, this has been the primary factor in the rise of the sending sexual images to others. It is under the label of ‘Sexting’, this is a culture that has risen with the rise of social media.
According to a BBC report from 2017[2], which emanated from discussions with the Police in the UK. Thousands of children, with some as young as 5 years old have been investigated fir ‘sexting’. Furthermore, figures stated that there has been ‘4,000’ Police cases between 2013-2017, in relation to the new phenomenon of children/teens sending explicit sexual images and sending to other young people. This shows just how frighteningly usual sexting is getting with children.
In addition to this, from Smith, Davidson and Thompsons paper, ‘Cyber Safety for Adolescent girls’. Which was referenced in Andrew Murray’s Technology Information law book 3rdedition[3]. It states that; in the UK ‘12%’ had suffered peer pressure to send images, where as ‘4%’ had sent images as a result of this. This worryingly breaks down to ‘444,000’ children between the age if 11-16 receiving these images. In addition to the even more frightening prospect of, ‘148,000’ children generating and sending such images in return.
Thus, highlighting how ‘sexting’ has become a major issue and how it directly links to revenge porn as many of these images shall be sent on or uploaded without consent of the senders of the pictures.
Historical Development
With a thorough introduction to what revenge porn and sexting entail, highlighting what a major issue it is becoming in the modern era. This blog shall now delve into the background and development of law in relation to revenge porn.
In relation to Sexting and in particular under the age of 18, this is dealt with by the Protection of Children Act 1978[4]and the Criminal Justice Act 1988[5]. Both of these acts can be useful in many cases, such as sexting from a person over the age of 18 to someone under that age. However, the major fault in the legislation is, as most of the senders and receivers involved in sexting are both under the age of 18. The laws do not allow the full brunt of law to be brought down upon them, leaving major gaps in terms of dealing with sexting, which as discussed is the main method of starting revenge porn.
In terms of with Revenge porn itself[6], it comes predominantly through 2 ways; the first is websites online that depict pictures uploaded of normally peoples ex girlfriend/boyfriends and the second is more direct and is the same types of photos being posted on social media.
The first, has been a major problem with several sites being produced and images being uploaded. One of the most famous cases in this field comes from Hunter Moore 2015[7]. in this American based case, a cite called ‘IsAnyoneUP.com’, the website contained several images uploaded of ‘ex’s’ depicting them nude or in videos. In addition, it was found many of the uploaded images were as a result of hacking into people’s pictures to find images and upload them. Subsequently Moore was charged with both computer misuse and identify charges. In 2015 he pleaded guilty to the charges, resulting in him being fined ‘2,000’ dollars and sentenced to 2 years’ imprisonment. Thus highlighting how serious revenge porn is handled globally in these cases. However, with many similar sites still active and these types of images freely going about it is argued more can be done to stamp it out.
In relation to the second main type of revenge porn, it is a more personal and arguably causes greater physical and psychological damage to the victim. It entails usually ex’s posting images to social media, often tagging the victim which depicts them in a nude or semi nude state. Prior to the England and Wales legislation of, Criminal Justice and Courts Act 2015 S.33-35[8]and Scotland’s Abusive Behaviour and Sexual Harm Act 2016 S.22. It was extremely hard to legally deal with revenge porn, as it was not legally dealt with under a specific piece of legislation.
A case that highlights this clearly is, the case of AMP V Persons Unknown 2011 [9]. In this English case, a girl had her phone stolen and indecent images stolen from it and uploaded. In the tackling of the case she had to use a mixture of copyright law and the protection of harassment act to peruse a case, as pervious to the case being taken forward anyone who uploaded the images was not committing an offence. Thus, the case under these legislations gave the women control over the images to formally notify suppliers of the images that a breach of the court was occurring.
This highlights how iritic the law was in terms of revenge porn only a few years ago and how far it has came in recent times with new legislation, in addition it shows how new an area of law it still is and how it shall take time to fully get on top of it in relation to law.
Review of Current law
In relation to the current law as previously mentioned, for England and Wales it is brought in by the Criminal Justice and Courts Act 2015 Sections 33-35 and, the Scotland Act of Abusive Behaviour and Sexual Harm 2016 Section 22. The legislation’s brought are essentially the first that directly deals with and engages revenge porn head on. Thus, it is arguable that the law shall not be perfect and there shall be some kinks in it to be ironed out throughout future precedent and amendments made.
Furthermore, with the legislation being so new it is difficult to calculate how successful it has been thus far. However, some developments have clearly been made in the early days of the legislation. In relation to the England and Wales act it has had some early success, this was highlighted in a BBC report from 2016[10]. In this report it details how; more than ‘200’ people had been prosecuted under the act since its inception a year prior, entailing maximum imprisonment of 2 years. This shows a clear impact as previously the offences were more likely to go unpunished as a result of no clear legislation to protect victims. However, as the report goes on to also state, freedom of information responses from 31 of 43 Police forces in England or Wales, stated that there was ‘1,160’ reported incidents on revenge porn in a time frame from April-December 2015. This is startlingly high, in addition a frightening stat of ’61%’ of the cases resulted in no action being taken. Thus, making clear that although some strides in the right direction had been made by the new law, the issue was still predominantly unresolved in England and Wales.
In relation to Scotland’s answer to revenge porn in the 2016 act, another BBC report in 2018 written by ‘Marc Ellison’[11]. In this report it details the shortcomings of Scotland’s 2016 law, in relation to July-December 2017. ‘225’ complaints were lodged to Police regarding revenge porn in Scotland. However, only ‘89’- which equates to the extremely low ‘39%’ were actually referred to prosecutors. In a continuing theme a third of the cases were concerning teenagers. Thus, highlighting how vulnerable people are not getting sufficient protection in cyber space under these laws. In regards to Scotland, England and Wales, leaving young people open to suffer from revenge porn with less not a great chance of gaining a conviction under these new legislations.
Overall, it is early in relation to these laws and they are essentially the first of their kind in this specific field. So it is clear they won’t fully get on top of revenge porn over night. However, the acts do clearly need to gain further control over an ever growing offence which is extremely affecting young and vulnerable people.
Lessig’s Modalities of Regulation
Lessig’s modalities as explained in part A and in this YouTube clip by Lessig himself[12]…
https://www.youtube.com/watch?v=EXOv1doHp88&feature=youtu.be
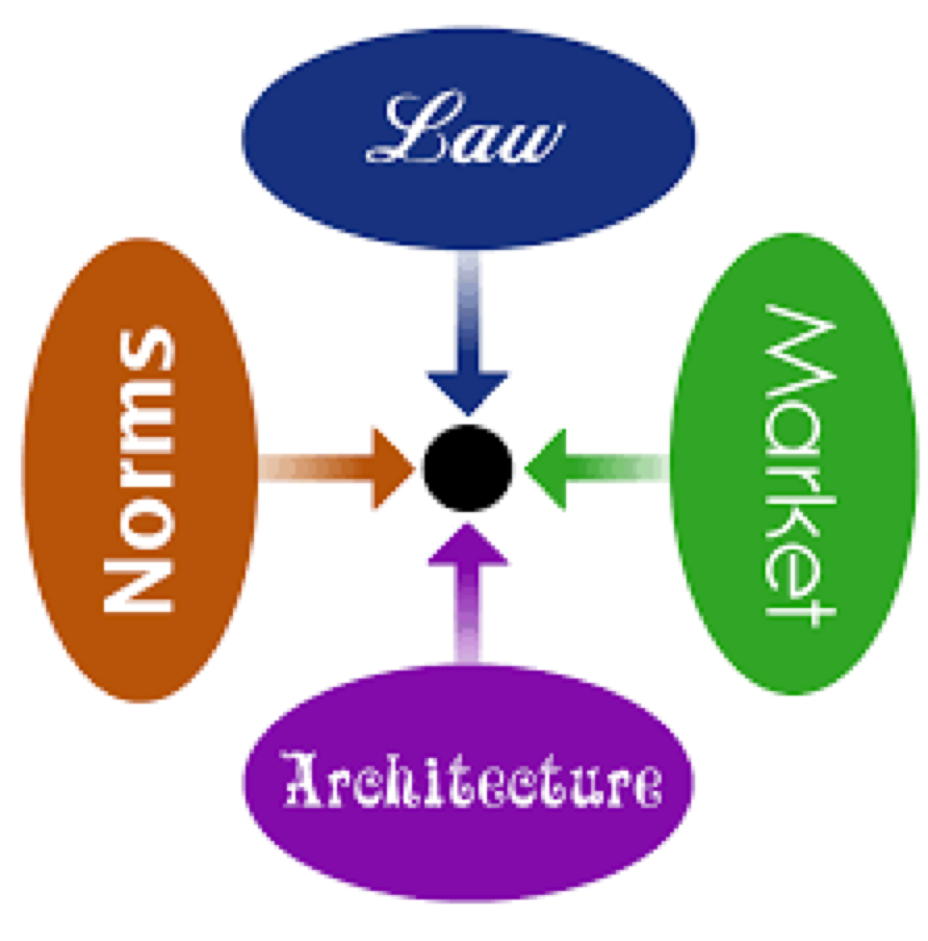
Is in relation to; Law, Market, Social Norms and Architecture.
Law as discussed, has had developments in terms of stopping revenge porn and stamping down upon it. However, extensive research has made clear that the new legislation, at the time of this blog are not doing a sufficient job in stopping revenge pornography.
Market in terms of revenge porn cannot strongly influence or prevent revenge porn, thus is not one of the most important factors in this scenario.
However, social norms do have a major part to play. This is for social norms put constraints upon people psychologically, if it is deemed as socially unacceptable to upload these images, causing more people to be chastised for it. Then ultimately many shall not participate in revenge porn, this sadly at the current moment is not always the case, with many people visiting cites in order to look at and or share the images further. This makes certain individuals feel, it is almost acceptable to upload these images and must be stamped out.
In relation to Architecture, which is normally the most important constraint to prevent cyber crimes. For the unique case of revenge porn, it is arguably less prominent and important than other factors such as social norms and law. This is for many of the images posted online are taken and at the time freely provided to the receiver, through the format of ‘sexting’. Only for later that person to betray them in posting the images, thus it is very hard for architecture to foresee and deal with this form of illegality. However, it can still play its part, by warning young people in particular of the dangers within application such as Snapchat of sending these images. Furthermore, more can be done to educate the person committing the offence as to the consequences on distributing these images, both to the victim and the legal ramifications they bring upon themselves.
Conclusion
To conclude, it is clear from this blog through extensive research, that the current law in this field is suffering from being new and at the forefront of the fight on revenge porn being the first of its kind. However, as previously stated much more needs to be done and developed upon to help prosecute and protect against revenge porn, in particular on young people who are often the victims of this crime. In addition, in relation to Lessig’s regulations social norms and law, with some input from architecture have a major role to play in terms of condemning and showing action shall be taken on anyone participating in the crime of revenge porn. Only then can an authority, really be stamped upon this wildfire of a relatively new and very serious cyber crime.
References Primary + Secondary Sources
- The Cambridge Dictionary><Revenge Pornography Definition<
- BBC.co.uk><https://www.bbc.co.uk/news/uk-40566026<>’Thousands of children sexting, police say> Published July 11th2017<>Last Accessed 10thApril<
- Information Technology Law 3rdEdition by Andrew Murray y> Oxford Press 2016<> Chapter 14.5<
- The Protection of Children Act 1978 c.37><>Legislation.gov<>https://www.legislation.gov.uk/ukpga/1978/37<>Last Accessed 10thApril<
- The Criminal Justice Act 1988 c.33>Legislation.gov.uk><https://www.legislation.gov.uk/ukpga/1988/33/contents<>Last Accessed 10th April<
- Information Technology Law 3rdEdition by Andrew Murray y> Oxford Press 2016<> Chapter 14.5 page 419<
- Washingtonpost.com><https://www.washingtonpost.com/news/the-intersect/wp/2015/12/03/revenge-porn-purveyor-hunter-moore-is-sentenced-to-prison/?noredirect=on&utm_term=.bcd01107043b<>Hunter Moore case 2015, ‘IsAnyoneUp.com’<Last Accessed 10thApril<
- Criminal Justice and Courts Act 2015 c.2, S.33-35>Legislation.gov.uk<>http://www.legislation.gov.uk/ukpga/2015/2/contents/enacted<>Last Accessed 11th April
- AMP V Persons Unknown (2011) EWHC 3454
- BBC.co.uk<>https://www.bbc.co.uk/news/uk-37278264<>’Revenge Porn: More than 200 prosecuted under the new law’ September 6th<>Last Accessed 11thApril<
- BBC.co.uk><>https://www.bbc.co.uk/news/uk-scotland-42689607<> ‘Less than half porn cases passed to prosecutors’, by Marc Ellison 6thof March 2018<>Last accessed 11thApril<
- Youtube><>https://youtu.be/EXOv1doHp88< By The Berkman Klien Centre for Internet & Society<> Published August 5th2011<>Last Accessed 11thApril 2019<
Footnotes
[1]Cambridge Dictionary- Revenge Porn Definition
[2]BBC.co.uk report ‘Thousands of children sexting, police say’
[3]Information Technology Law Book by Andrew Murray
[4]Protection of Children Act 1978
[5]Criminal Justice Act 1988
[6]Information Technology Law 3rdEdition by Andrew Murray
[7]Washington Post Hunter Moore ‘IsAnyoneUp.com’ case
[8]Criminal Justice and Courts Act 2015 S.33-35
[9]AMP V Persons Unknown 2011 EWHC 3454
[10]BBC report ‘Revenge Porn…’
[11]BBC report by ‘Marc Ellison’
[12]Lawrence Lessig Four types of regulation- YouTube